
With the introduction of social distancing and uncertainty over what the future holds, businesses are looking to change the way we work more drastically than ever before. However, there is a historical precedent, 355 years ago in 1665, an outbreak of bubonic plague, caused Cambridge University to close and as a result Isaac Newton was forced to "work from home". It was during his time at home he made major discoveries in gravity and calculus. Things may look daunting now, but if we work together and support each other maybe we too can make some amazing discoveries in this time of forced isolation.Luckily, many organisations have already been trialling remote working; however, this has always been on a much smaller scale. Never before have companies been required to make such large proportions of their workforce operate from home.
This is creating a strain on existing infrastructures, as the number of people working remotely is drastically increasing with most office based companies working from home wherever possible. These changes are no longer happening at a steady pace and the rush to adapt to the new situation could easily cause measures to be put in place incorrectly. Malicious threat actors will take advantage of this to launch increased cyber attacks at weakened defences.
Problems encountered working from home enmasse
There are a whole host of problems facing the UK workforce and not all of them are IT based.
Increased Cyber Attacks
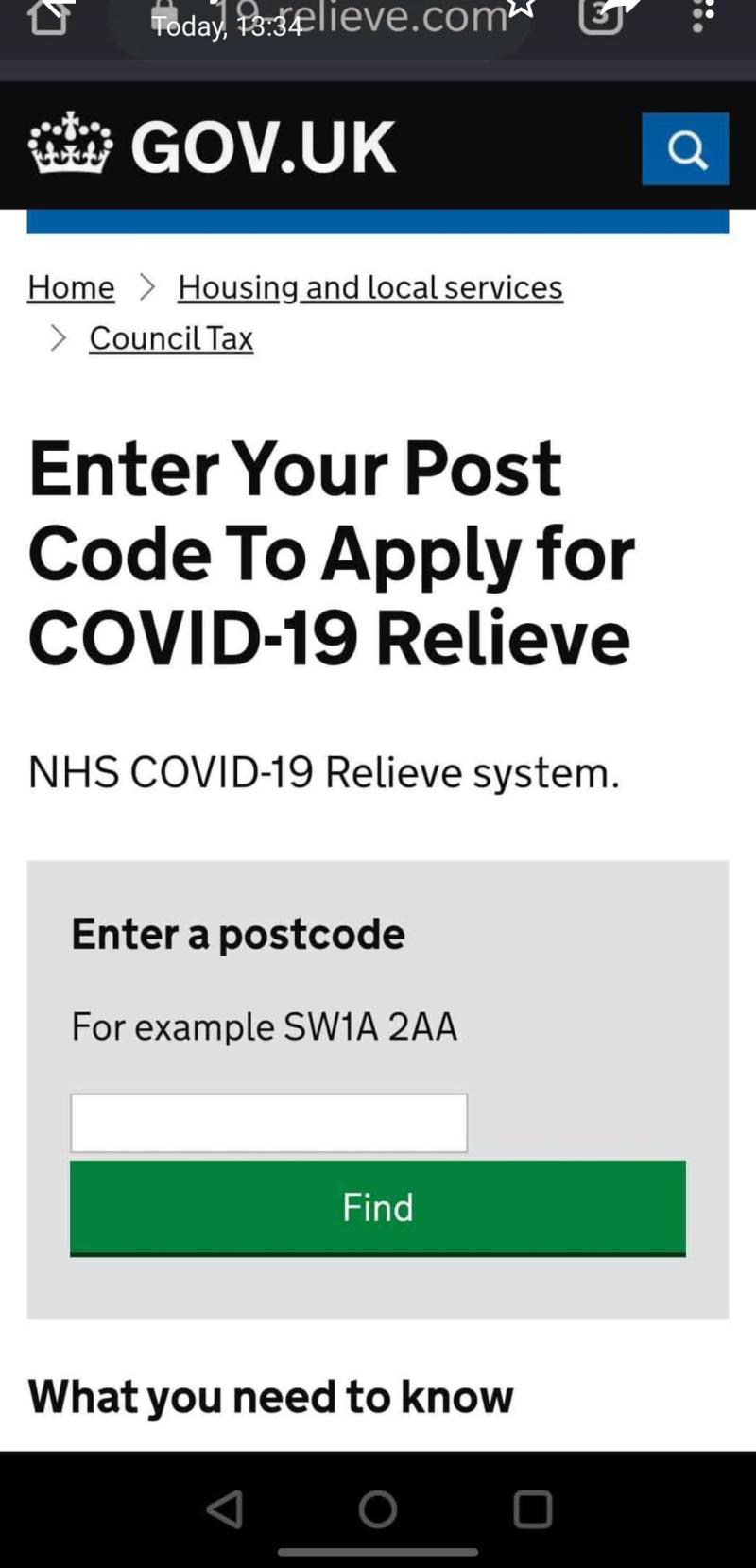
Cyber criminals are always looking for new attack vectors and exploiting public emergencies is a common tactic. Covid 19 offers an attractive opportunity to exploit people’s growing fears. This email forgery impersonating the US CDC is a good attempt. There have been multiple reports of fake news articles and site spoofing adding to the overall panic surrounding Covid-19 and making it harder for people to find legitimate information regarding recommendations and advice. A new addition to this has been the addition of fake sites claiming to be UK.GOV to provide business government Covid grants, or apply for HMRC to cover salaries. Be sure to keep an eye out for these and don't fall into the trap. Successful attacks could prove to be very problematic to companies since their employees’ personal networks will be much weaker than the enhanced protections surrounding a corporate network and thus may not be sufficiently protected.
Also, it is highly likely that hackers are exploiting remote help solutions. For example, by gaining access to remote help software allowing companies to connect to a user’s PC at home and maintain it. The following is an example of what this could look like: “Hi, I’m from your IT department, we see you have a remote working issue. Please go to this web site, and press authenticate to allow me to login in and sort it out for you.” Companies should create clear procedures and policies to ensure that all employees understand how IT support will try to fix their devices. They should also create an authentication process that will allow them to confirm that the person contacting them is genuine.
Reduced Human Interactions
Social distancing, isolation and home working is drastically reducing the amount of human interactions people make on a daily basis. The positive impact of social interactions on both a physical and mental level can improve our ability to cope with stress. Understandably a pandemic is a very stressful event and being isolated means we also need to think of ways to have social interactions that do not require physical proximity. We need to isolate to ensure that the spread of the virus is limited and we protect vulnerable groups from becoming infected. So to help manage the stress and the loneliness we advise you to take advantage of technological advances like Facetime and call your friends and family more often than you usually would. If you do happen to live with other people, make time to play games or interact with each other to lift the mood and encourage laughter.
Increased Video Conferencing
Infrastructure providers are struggling with the huge influx of users, and some are scaling back advanced features, to ensure a basic service is delivered. These infrastructure providers include video conferencing capabilities. It is worth noting that with the increased use of video conferencing, we are all getting to see what our colleague’s homes look like – at least the room they are working in (Kitchen, Bedroom…). While this is quite an exciting addition to live in isolation we would advise users to check what is visible in the background of their video. We have already seen one report of sensitive information in the background being “leaked” via video conference. If there is sensitive information that you can’t hide, products like Microsoft Teams offer a “blur the background” feature which can be enabled.
Finally, remember you can only record video sessions with the explicit permission of all participants. So ensure you ask all participants before hitting that record button.
Measures that you can take
In times like these it is important to do the basics really well and then do the added value extras. If your foundations are not strong it's likely that any additional measures will be undermined and fail in the end. So what are the basics?
If employees are now given remote access to systems that were previously only available in the office, then reiterating advice about password hygiene (e.g,. unique passwords) is essential. If the new “remote” systems are using the same password, then a “phish” on an employee’s home systems could compromise work systems.
Enable 2FA
Two-factor authentication (2FA), occasionally referred to as two-step verification and Multi-Factor Authentication (MFA), is a security process in which users provide two different authentication factors to verify themselves. Enabling two-factor authentication on all accounts employees use to access sensitive company data provides a higher level of assurance than authentication methods that depend upon single factor authentication. Two-factor authentication methods rely upon the users providing a password and a second factor, this will usually be a security token or a biometric factor such as a fingerprint or facial scan.
PAID for antivirus
Most free antivirus software should offer all the core tools you really need to keep your computer safe from internet threats. However the paid for versions are much better and often come with additional extras that can really boost the security of your system. For example, many paid for antivirus applications now include a password manager. You can also get stand alone password managers like Keepass or Lastpass, which can be used to generate and store multiple passwords. This means the user only needs to recall a handful of unique passwords and the rest can be stored in the password manager. This will help prevent employees from writing down the password or storing it in unsecured locations. Many corporate AV licences will allow for the paid version to be used on home computers, it is worth checking if that is true for your company.
Enable and Use Guest Wifi
The average UK home now has 10.3 internet-enabled devices (Aviva, 2020) with some of those devices including IoT technologies like CCTV or Smart TV. With varied access levels to the network it's hard to know how secure your home network really is. Most home routers have a guest Wi-fi, so a smart step to take would be to advise employees to connect the work equipment to the guest wi-fi only. This way, if their home systems are compromised, then the risk of malware spreading to the work PC is reduced.
If you would like more information the NCSC has recently updated their guide to Mitigating malware and ransomware attacks.
How Nexor Can Help
Nexor Cyber Security Assessment
As an SME ourselves we understand the challenges small businesses face, but are advantaged to be able to bring our own secure remote working capability from the Defence & Security sector to help others. If you need your workforce to be able to work on Company Confidential, Commercial-in-Confidence, OFFICIAL or OFFICIAL SENSITIVE files at home using Office365 then please get in touch.
If you have been a victim of fraud or cybercrime, report it to Action Fraud via their website https://www.actionfraud.police.uk/, or by calling them on 0300 123 2040.
You can also contact the Citizens Advice Consumer Service for consumer advice by calling 0808 223 11 33.
For anyone concerned about COVID-19 please refer to the NHS advice page - https://www.nhs.uk/conditions/coronavirus-covid-19/

