
First of all, let's introduce ourselves!
Nexor is a company full of passionate, knowledgeable, and intelligent cyber-security professionals, who take cyber- security very seriously. We have an impressive track record in working with our customers to build solutions that match their security needs, utilising our suite of products based on NCSC architectural patterns and secure software and hardware development practices. We truly do care about our customers and their security stories, and we have the credentials and history to back up our customers at every step of their journey.

Hardsec: Security from the Start
An emerging concept in cyber security is "hardsec," which aims to switch the primary focus of cyber-security from software to hardware. Hardware security sits at the root of the physical part of a system, protecting its basic components. An example of this is a hardware security module (HSM) that can be used to provision cryptographic keys to encrypt, decrypt, or authenticate user identities.
Vulnerabilities in cyber-security are regularly the cause of serious damage to companies’ bottom lines, countries' economies, and individuals’ privacy. These damages usually originate through software exploitation as this is the easiest point of attack. Stated simply, "The risks to both business and nation from failing security policies and products make the investment in better security technologies more than a measure of cost effectiveness, but of necessity."
So why is it better to build security into the hardware itself? A 2018 report issued by The Council of Economic Advisers states "that hardware is a less frequent target of hackers than software for a number of reasons:
Hardware is less easily accessible;
Hardware is not as well understood (as software);
Attacks against hardware must be highly specialised.
Therefore, the benefits of building security into hardware are:
Ensures trust in end devices and components rather than building software on top of these devices and components that can be exploited.
Hardware will be more difficult to exploit, as it requires a deeper technical understanding, is more time consuming, and requires access to the hardware from the source.
Hardware is "dumb," which sounds like a negative, but means there is a vastly reduced attack surface. General purpose processors were designed to be flexible to run any code and unfortunately, if exploited, the code that is running may not be what was intended by the designer. An FPGA implementation is designed in configurable hardware to do a specific task which makes it much more difficult to subvert.
Protect - Hardware at Nexor
Hardware can add a physical layer of protection to software's transformation, that substantially increases the difficulty for threat actors trying to modify it for criminal purposes. Nexor capitalises on this potential for inherent security to protect our customers from advanced cyber threat actors and enable the secure exchange of sensitive information between domains. While software does provide an invaluable service to many government and commercial institutions, hardware’s capacity for inbuilt protection of technology components allows security to start from the very beginning of the process whilst providing additional benefits, such as performance improvements and scalability.
The UK Research Institute in Secure Hardware and Embedded Systems (RISE), which is partially funded by the National Cyber Security Centre (NCSC), have stated their focus "is to accelerate the industrial uptake of the Institute's research output and its translation into new products, services and business opportunities for the wider benefit of the UK economy." At Nexor, we have also embraced this focus to take advantage of hardware's vast capabilities when building solutions for situations that have challenging performance and scalability requirements. The Nexor Citadel cross domain desktop, for example, provides a secure remote desktop solution by using hardware validation to police the boundary between networks of differing classifications.
An area of hardware technology where Nexor has invested significant research is FPGAs (this is an integrated circuit that can be customised for a specific application. Unlike traditional CPUs, FPGAs are "field-programmable," meaning they can be configured by the user after manufacturing). We recognise that secure FPGAs could be applied to multiple use cases in various industries, which makes it a compelling technology to focus on. IBM, Amazon, and Microsoft, among others, have already started adding this to their portfolio.
Why choose hardware?
Performance
When a solution needs high throughput and low latency content verification, moving the security enforcing function to hardware can provide significant advantages over software. It reduces the overhead on supporting software components, therefore increasing performance of the solution. A use case for this would be a protocol being enforced through an FPGA:
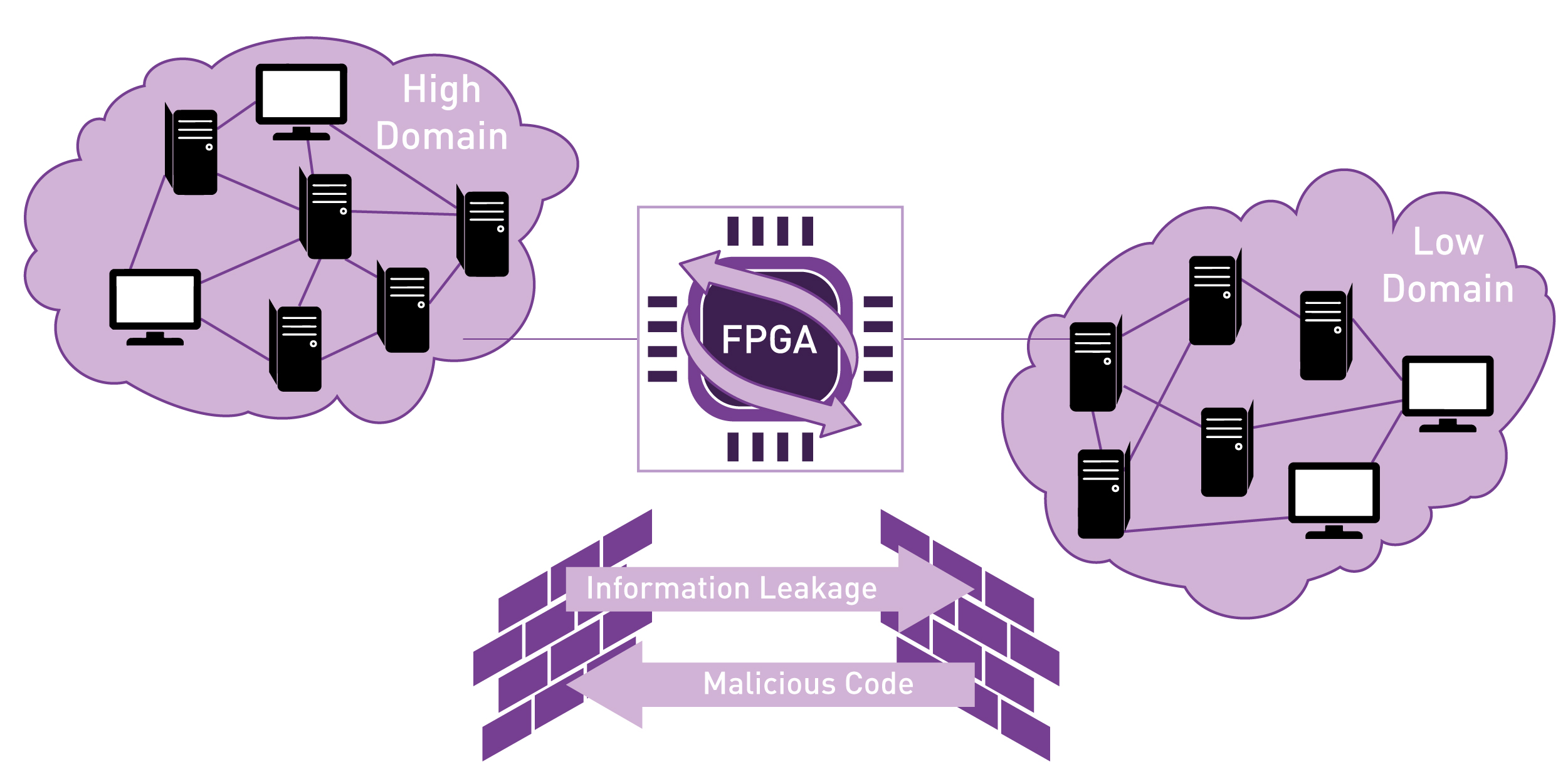
With an FPGA, the security enforcing function is validating that the correct protocol is flowing through the FPGA and is allowed out the other side. Because this is done in hardware, and the FPGA is performing a single function, the processing time is significantly reduced, allowing for higher performance throughput.
Protection Environment
The Hardware Root of Trust ultimately means that security is incorporated at the design phase and that security is built into the foundation. This results in fewer data vulnerabilities due to built-in fail-safe protection measures and anti-tamper mechanisms to lock the hardware down and revert it to a safe state when it has been improperly tampered with. Security functions are inherent in the hardware, which lessens the risk of vulnerabilities being found in updated software versions, which require constant monitoring and patching.
Additionally, there exists a reduced attack surface for hardware, as the FPGA functionality is dedicated. If a threat actor did manage to break part of it, it wouldn’t necessarily break the whole thing. With software, there are ways to escalate privileges such that once the threat actor is root (able to access the guts of the system), it’s game over. Hardware, more specifically FPGAs, cannot be "owned" in the same way as software, as it must be physically accessed in order to reprogram it to run malicious code. There are ways that FPGAs can be re-programmed over a network, but in a security sensitive application, that feature would be considered very carefully and weighed against the security risks.
Scalability
In some use cases, such as video processing, processing large amounts of data in software can cause unmanageable overheads, as it takes time and resources to do the processing function. In the case of a hardware implementation, some of that processing can be offloaded to the hardware in parallel, which significantly reduces the overhead on the software to do the simple computational elements required in processing data.
As data becomes more and more complex, in the vein of "Big Data," scalability and performance of data processing and analysis will become more pivotal to businesses and governments, and offloading the responsibility of processing the data to parallel hardware solutions is one answer to the "Big Data challenge." Additionally, the security element of sharing and collaborating across domains continues to be an element to consider, so providing a security enforcing function, as well as scaling to handle big data, can be managed in hardware implementations over software.
What happens when hardware is not adequately secured?
A lack of awareness or devotion of resources to hardware security can have severe consequences. An example of this is a serious hardware exploit called the Meltdown hardware vulnerability that, according to Ars Technica, "enables a wide range of information disclosure from every mainstream processor, with particularly severe flaws for Intel and some ARM chips."
The threat came to light in January of 2018 when the security community reported of a discovery by Jann Horn of the Google Project Zero project, Werner Haas/Thomas Prescher of Cyberus Technology, and a team at the Graz University of Technology. The basic premise of the attack was a breakdown of isolation between user applications and the operating system, which allowed a rogue process access to the system's memory (including passwords, user's personal information, and other secret data).
At the same time as the Meltdown attack was being discovered, a similar vulnerability called Spectre was identified, which affected Intel, AMD, and ARM processers. The nature of the exploit is to trick innocent programs into leaking private data, which leaves open a side door from which nefarious actors can steal information. To mitigate this risk software patches by processor manufacturers were dispatched, but performance was massively affected, and the patches did not fully resolve the threat.
Many threat actors are interested in using the Meltdown and Spectre exploits (and any variations thereof), however they are coming up against difficulties. Many machines have already been patched and there's a limited amount of data that can be obtained from an exploited machine. So far there have been no actual attacks that use the Meltdown and Spectre exploits, although researchers have found more than 130 samples of malware that attempted to use them, but were either test or proof of concept code.
It is important to remember that security threats exist at every level of a computer system, and there will always be cyber criminals attempting to bypass protections that prevent the leakage of sensitive information. Ultimately, the goal of cyber security is to outwit them and focusing on hardware security makes this endeavour significantly easier.

