You may see the term ‘threat actor’ within risk assessments or other articles - but what is a threat actor? Threat actors are people or entities who are responsible for an incident that impacts the cyber security of another person or organisation. Cyber threat actors use computers, systems or networks to cause disruption or harm with a wide range of underlying motives.
Cyber threats, carried out by threat actors, are more prevalent than ever. Recent government data suggests that up to 46% of UK businesses have suffered a cyber attack or breach in the previous 12 months. This reality puts the need for effective cyber resilience policies front and centre, and a vital step in any cyber resilience initiative is understanding the threat itself.
Threat actors usually seek out to do one of the following things:
Make financial gains
Increase their reputation or notoriety
Effect political, ideological or social change
Carry out political, economic or military espionage
The impact a cyber threat actor has depends on their resources, motivations and, above all, skills. As the abilities of threat actors adapt, so must the cyber security protocols of businesses and individuals. Any business that holds sensitive information is at risk of being targeted, which is why it is important to know the different types of threat actors and how to combat them.
What are the threat actor types?
While the methods used by threat actors can be similar, their goals and motives are often vastly different. However, most fit into the following broad categories:
Cyber criminals
Cyber criminals usually target organisations for financial gain. This is perhaps the most common type of threat actor, as studies have shown that cyber crime costs the global economy $2.9 million every minute. The methods used by cyber criminals range from basic tricks like phishing and denial of service (DDoS) to sophisticated malware. Their goal is to exploit insecure systems and human error to steal personally identifiable information like credit card details and social security numbers to commit fraud or blackmail.
Hacktivists
Hacktivists are a type of threat actor often mentioned in the media. Loose organisations like Anonymous have carried out cyber attacks on groups like ISIS to bring about social, political or ideological change. These people often hack into systems to expose incriminating information about an organisation, person or group to the wider public.
State-sponsored hackers
Hackers that are backed by the resources of a nation-state are often the most dangerous type of threat actor. Using tactics like DDoS, cyber reconnaissance and advanced malware, state-sponsored hackers are able to access company data that they can use to influence whole industries on an international scale. Their access to large amounts of financial backing means they can be difficult to defend against in the long term. The 2017 NotPetya ransomware attack by Russian-backed hackers caused mass power outages and led to the loss of important data, and is just one example of the devastating effect of this kind of threat actor.
Script kiddies
This type of threat actor is known as a script kiddie, a term attributed to individuals with elementary hacking skills and who launch existing scripts to deface a website and simply cause disruption for entertainment. Businesses targeted by script kiddies can incur severe costs to repair systems and recover data, unless the appropriate precautions are taken.
Disgruntled employees
Human error is often cited as the most common source of a data breach, yet an often overlooked threat is the risk of a disgruntled employee causing damage from the inside.
The risk of an employee with privileged access to data using that access for their own gain is a serious issue to prepare for. With so much of cyber security being focused on keeping outsiders out, little attention is paid to monitoring and preventing those already inside from causing disruption. The methods used by disgruntled employees are often elementary, such as downloading payroll information onto a USB or printing sensitive financial data, but the effects can be devastating.
What is the best defence against threat actor attacks?
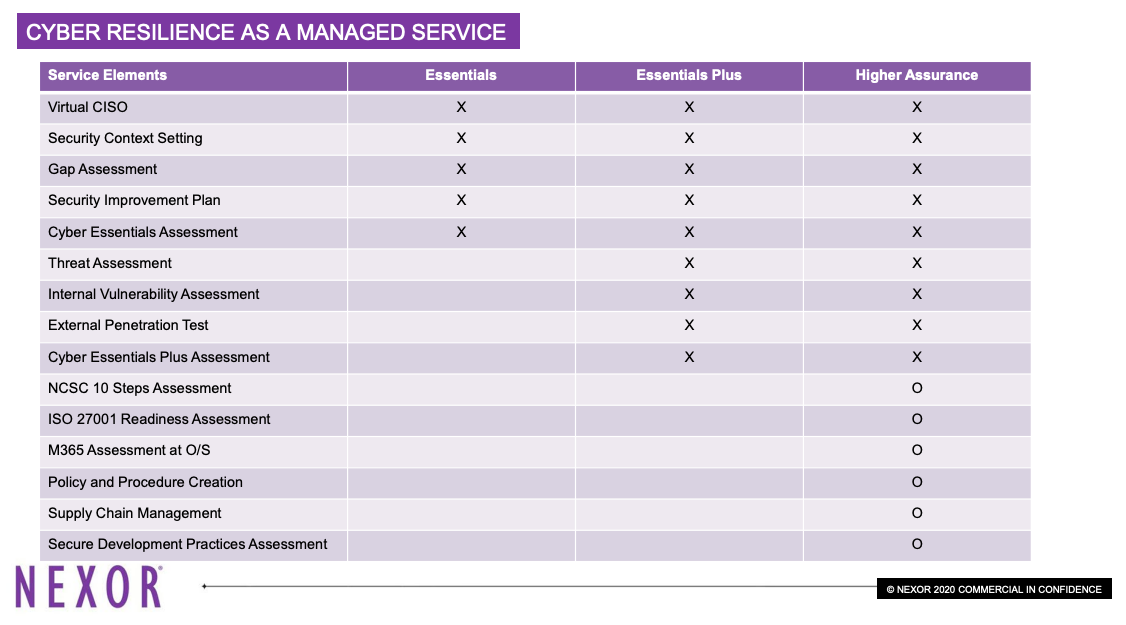
It is essential that businesses take the necessary precautions to protect their sensitive data, else risk significant financial and reputational damage. If you haven't done so already a starting point would be the Cyber Essentials certification. This is a UK Government backed scheme to protect organisations of any size against a range of the most common cyber attacks. It provides a baseline set of technical controls and a lightweight and easily manageable process that leaders can navigate through.
The certification has two tiers:
Essentials
Essentials Plus
This certification is a cost-effective way of safeguarding an organisation from a cyber attack. Studies have shown that the implementation of Cyber Essential fully mitigates 70% and partially mitigates 29% of all cyber attacks, not including state sponsored actors.
Nevertheless, the best long-term solutions require a higher level of preparedness, possibly including the likes of the NCSC 10 Steps Assessment and the M365 Assessment. If your business would benefit from a higher level of security, enquire with a qualified provider of Cyber Resilience As A Managed Service.