
Diodes are Diodes, Guards are Guards
Over the last 3-5 years Data Diodes have grown in popularity as a solution for moving data between isolated networks. With this has come creative marketing to leverage the term 'Diode' for solutions that are anything but.
Let's just take a few moments to revise some of the fundamental modes of secure information exchange.
Protecting Secrets
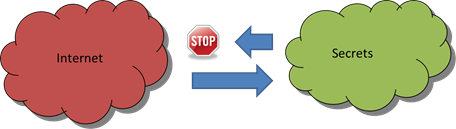
If you want to share information with a network, but that network has secrets to protect, the highest level of assurance you can obtain is to use a Data Diode to ensure information can only flow left to right as demonstrated in the diagram below, and not right to left.
The Nexor white paper Protecting confidential information using Data Diodes describes how this works in detail. It also describes how content filtering works to ensure only a restricted subset of data is allowed over the connection.
This is a common scenario in high security government and defence networks.
Protecting Assets
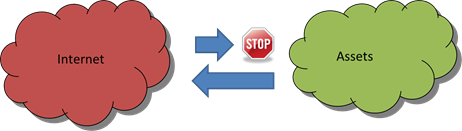
This is the reverse of the Protecting Secrets scenario, here there is data produced by the Assets that needs to be shared, but the network you are sharing with cannot be allowed to influence the assets in any way.
This is a common scenario in high integrity industrial control systems, such as power generation and transport infrastructures. Here too, if you want the high level of assurance, Data Diodes are used.
One way data, with protocol handshake
One of the difficulties with the diode approaches above is that the underlying communication protocol is often two way. The paper Protecting confidential information using Data Diodes identifies how you can overcome this with a data diode. However, in lower assurance environments, the feedback is useful as it provides a mechanism for saying something has gone wrong. A good example is an email exchange – you want to know it has been delivered. The compromise is that by providing a feedback loop you are reducing the assurance – you have fundamentally implemented two way communication. In this case you need a two way data exchange solution, not a data diode.
Two way data exchange (synchronous communications)
When you absolutely need two way communications, then diodes do not have a role. This is where Data Guards come in – special purpose appliances designed to allow the data flow, while providing high assurance network separation and filtering. Note also the difference between a guard and a gateway.
Two way, asynchronous communications
In this mode of communication, you fundamentally need data to flow both ways, but the information flows are not linked. A good example of this is described in the blog Secure Remote Camera Control where streaming video flows one way, and pan-tilt-zoom controls the other.
Here using diodes makes sense, as they are two independent data streams – it is hard (but not impossible) to create a two way information flow.
Complexity
This may seem complex, because it is complex; that is why we see so many security breach reports, security is hard. The critical element is to ensure you know what problem you are trying to solve, understand the threats, design a solution that mitigates the threats to an agreed level of assurance and is then implemented using best of breed products.
That's what we do at Nexor.
We don't try to dress a guard up as a diode, because that represents misinformation - integrity ought to extend beyond the data transmission!

