What is Cyber Resilience?
Cyber resilience is a new approach to security that recognises the threat of persistent, changing attacks. Organisations need a resilient cyber security strategy that enables them to respond to inevitable breaches, rather than hoping that their data will never come under threat.
Cyber resilience strategies have emerged as a response to the increasing number of cyber attacks and data breaches that have made headlines for the wrong reasons. The cost of a significant breach to an organisation’s operations, finances and reputation has never been higher.
Nexor’s CyberShield Secure methodology is one example of a resilient approach to cyber security. Our approach recognises the need for ongoing monitoring and adaptation within an organisation’s security solutions, in addition to ensuring that those solutions do not compromise the organisation’s primary business or operational objectives.
A Counterpart to Cyber Security
Cyber resilience is a crucial counterpart to cyber security, not its opposite. Rather than existing as a contrast to the concept of security, it is more appropriate to see cyber resilience as a contrast to an older security methodology: the ‘castle approach.’ Where this style of approach sought only to build defensive walls, cyber resilience strategies are designed to deal with breaches as efficiently as possible when they happen.
A resilient cyber security strategy should not be a pessimistic approach. Nexor’s solutions will always be designed to minimise the risk of threats occurring in the first place. However, no solution can respond to every threat, both online and human. Resilient strategies acknowledge this reality and provide ways to mitigate a breach’s impact.
Developing a Cyber Resilience Strategy
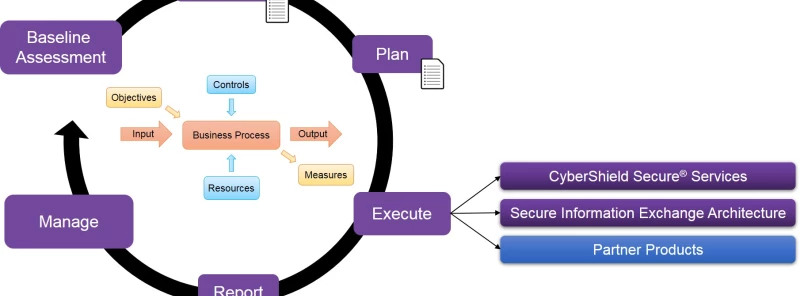
Cyber resilience strategies incorporate multiple stages that cover a long period of time. ‘Quick fixes’ cannot work where long-term adaptability and response is the end goal. Nexor’s CyberShield Secure methodology is an example of the kind of multistage strategy that promotes cyber resilience:
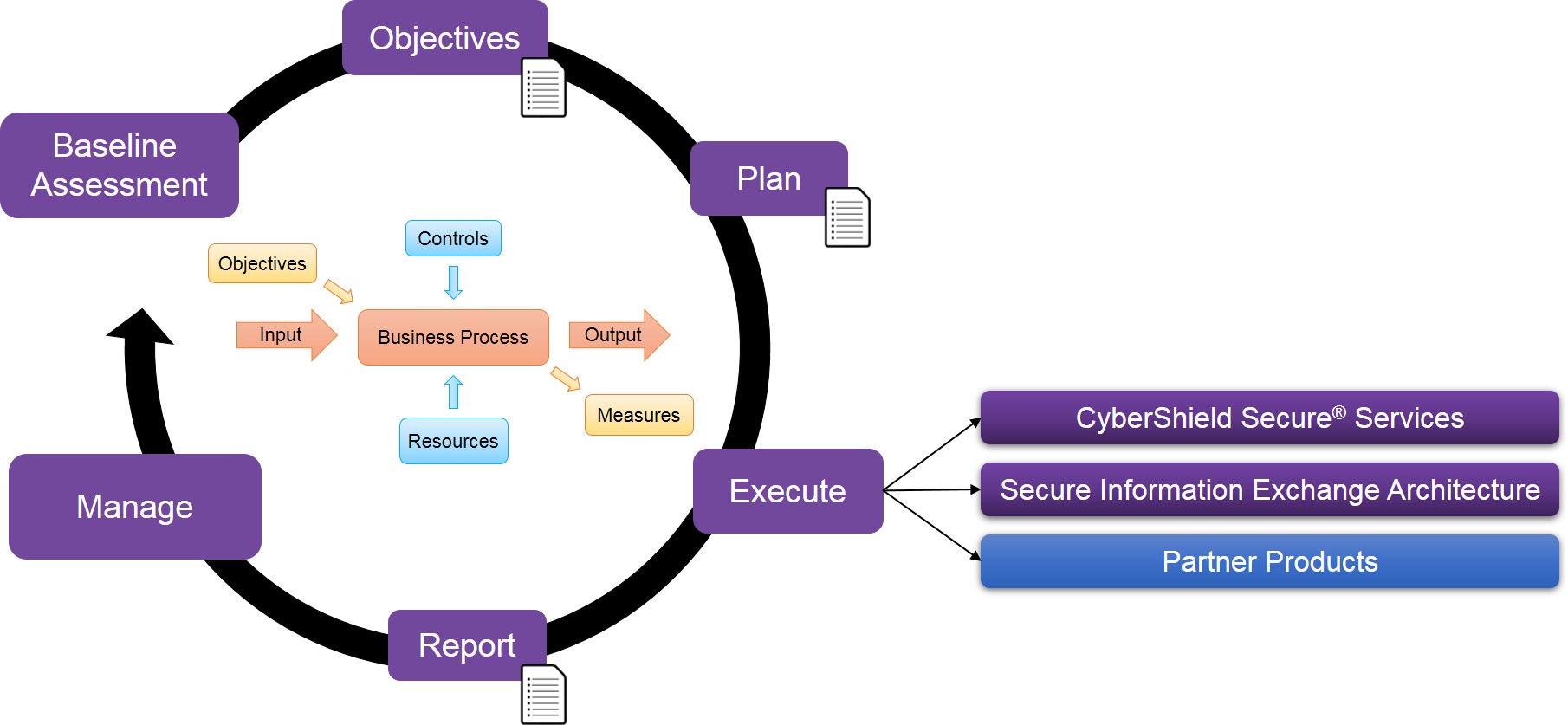
1. Baseline assessment
We will understand an organisation’s business requirements, their operational content, and determine how we can measure the success of our strategy.
2. Identify resources and controls
Our specialists identify the resources and controls necessary to improve the long-term security of the organisation and ensure that their operational objectives will still be met.
3. Create a plan
A crucial stage of any resilient process, we agree on an initial plan of action that could include some combination of cyber security consultancy or technological delivery.
4. Execution
We then deliver the action plan through a combination of our CyberShield Secure services, SIXA technologies and appropriate partner products.
5. Report
While older strategies might have stopped at the execution step, resilient strategies continue. We will summarise the outcomes thus far and make recommendations for continued management and improvement.
6. Manage
We will continue working with the organisation to ensure that their solution is performing as expected and that their organisation is set up to minimise the risks from cyber attacks. If necessary, we will return to step 1 to develop their security strategies further.
As our above diagram illustrates, Nexor’s CyberShield Secure methodology is a cyclical strategy. It does not end at execution or reporting, but continues into the future to allow the organisation’s changing experiences and needs to inform the evolution of its cyber security processes. In this way, their solutions will always be equipped to help them deal with current challenges.
Disaster Recovery and Business Continuity
An important part of cyber resilience is the ability of the business to continue in its mission even if attacked. Our approach includes ensuring that the organisation has a viable incident response plan, which needs to involve both disaster recovery and business continuity strategies.
Companies often make the mistake of conflating disaster recovery and business continuity, but they are fundamentally different. Disaster recovery involves stopping an attack and rebuilding the organisation’s computers so that they can be used again. Business continuity, on the other hand, is the ability for a business to continue as normally where possible while the affected computers are being fixed. Both are necessary parts of cyber resilience and neither make wider cyber security concerns obsolete.
Who needs Cyber Resilience?
The number of cyber attacks affecting British businesses mean that no organisation can completely ignore cyber resilience. SMEs cannot afford to assume that cyber attacks will only ever affect large organisations and the public sector; in fact, according to the latest figures, SMEs currently bear the brunt of 43% of all cyber security attacks. Businesses of all sizes, operating in all industries, have room to improve in this area.
SMEs handling sensitive information, like those in the defence supply chain, should be particularly alert to the present dangers and not neglect a cyber resilience strategy. It is essential that threats are identified as quickly as possible and that protection, recovery and continuity plans are put in place to ensure that an attack doesn’t spell the end for the business.
Benefits of Cyber Resilience
Organisations remain as close to ‘business as usual’ as possible, during and in the immediate aftermath of an attack;
Able to adapt to evolving threats;
Protect brand and reputation in the event of a breach;
Improve cyber security without constraining business agility.
Find out more about Nexor's cyber resilience strategies with information on our CyberShield Secure methodology and services.

