Booting Linux Securely
February 2014
A report from Learning Tree "Linux Scores Highest in UK Government Security Assessment" has analysed the CESG set of reports on the security of end user devices, in which CESG assessed 11 operating systems.
The Learning Tree report observed:
Of those, Linux got the best overall score
The report then looked at the criteria used to make this assess, and suggested:
As for Secure Boot, that has its serious detractors
The boot process is a chain of events, from the BIOS (or the more recent successor UEFI), though to the boot loader, which starts the operating system kernel, which in loads the kernel modules and provides the environment required to run the configured applications.
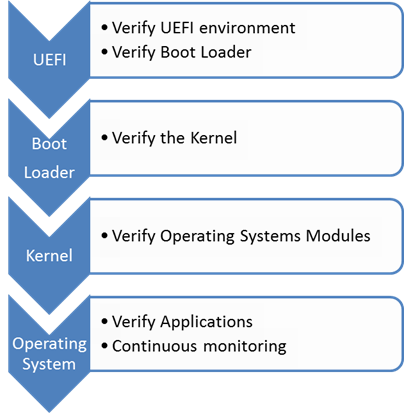
The Windows 8 boot process, is identified in the CESG documentation:
On Windows 8.1 this requirement is met on a correctly configured platform deployed on supported hardware. An EFI/BIOS password can make it more difficult for an attacker to modify the boot process.
Whereas CESG say the following about Linux (Ubuntu 12.04):
There is currently no secure boot mechanism in a standard Ubuntu platform.
Booting securely is important from a user perspective; it ensures that only an authorised person or application can modify the boot process of a device, thereby preventing malware such as bootkits and rootkits from infecting the device.
At Nexor, we have looked at this process in Linux and have successfully delivered a demonstrator to a customer that shows how a process similar to Windows 8 can be replicated in Ubuntu, largely using openly available components. In short, we used signatures held by the trusted platform module (TPM) to validate the UEFI environment, then UEFI extensions to start the boot sequence, with the integrity of each component loaded being checked at each step of the way, by way of signature validation, using both kernel and application level signing.
The role of the TPM is vitally important, as discussed in the IBM report "UEFI Secure Boot and the TPM" and its companion "UEFI Secure Boot and the TPM: Implementing Secure Boot with a TPM". The TPM provides a trust anchor, from which the integrity of the other elements of the boot process can be established via a trust chain. In addition the TPM can be used to enforce the boot sequence, using Linux Unified Key Setup (LUKS) to manage disk encryption keys and thus force a single boot path.
So while we agree with the CESG report with a standard Ubuntu platform there is no secure boot mechanism; we assert that with the appropriate knowhow this problem can be overcome and a secure boot environment provided, using open source components.
Can we help your business boot Linux securely?

